National Internet Day isn’t a feel-good milestone – it’s a mirror. One that reflects just how dependent we’ve become on a system we barely control. While most are busy posting hashtags, the sharpest minds are asking: what happens when the internet blinks?
40% of small businesses hit by attacks were down for over 8 hours. That’s not “downtime” – that’s dead air. Sales vanish. Clients panic. Ops freeze. If that number doesn’t scare you, you’re either fully fortified, or blindly optimistic. And in tech, optimism is the first point of failure.
Chad Cunningham, Owner and Partner of Ironclad TEK, states, “Security is the only innovation that’s invisible when it works – and unforgettable when it doesn’t.” That’s the paradox we unpack today. In this blog, we dive into the real reason National Internet Day matters: not because we’re connected, but because we’re exposed. Safety first. Always.
Every Click is a Threat or a Throne – Decide Which It’ll Be
National Internet Day: A Strategic Lens on Digital Risk Exposure
Each year, National Internet Day celebrates the technologies that power global connectivity. But for business leaders, it also presents a checkpoint to assess how secure that connectivity really is. This section examines how access, scale, and speed have created parallel vulnerabilities beneath digital progress.
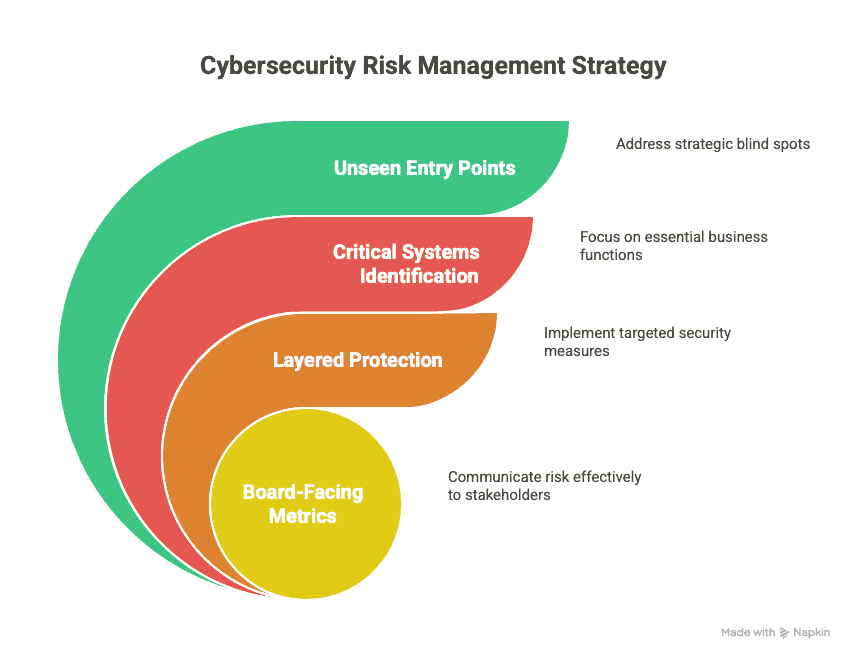
1. Unseen Entry Points Create Strategic Blind Spots
Even well-managed networks often fail to track lateral access.
- Third-party app connections bypass internal audits
- Misconfigured user roles allow privilege creep
- Guest access settings remain enabled after project close
2. The Overlooked Security Gap in Innovation Cycles
When speed is prioritized over scrutiny, exposure grows. Businesses should reassess controls after any platform adoption, merger, or major system integration.
3. Mapped Risk Tells a Clearer Story than Generic Coverage
Vulnerability isn’t about volume. It’s about context.
- Identify critical systems by business function
- Layer protection based on potential revenue impact
- Connect risk levels to board-facing metrics
National Internet Day should drive alignment between IT and executive teams. Progress only counts if it’s protected.
Downtime Economics: What 8 Hours Offline Actually Costs a Business
The speed of the internet disguises the fragility of what runs on it. During National Internet Day, the focus shouldn’t just be uptime – it should be the cost of losing it. This section explores the operational consequences of unplanned outages.
Outage duration is just a variable. Every week, 140,000 hard drives experience data loss in the United States. But for most businesses, the real damage is in response time – not failure itself.
Downtime Cascades Across Departments
When critical systems fail:
- Sales pipelines pause in CRM
- Accounting loses access to billing cycles
- Operations shift to manual processes
Calculating Cost Based on Real Conditions
It’s not enough to estimate averages.
- Determine impact per hour of downtime
- Assess affected headcount and service level commitments
- Add potential client churn or SLA penalties
Downtime is a boardroom metric, not just an IT issue. Executives should request quarterly downtime risk forecasts and test restore points before they’re needed.
Security as Infrastructure: Why National Internet Day Should Trigger a Policy Review
Few companies revisit their cybersecurity policy until something breaks. National Internet Day offers a reason to change that rhythm. This section focuses on positioning security policy as a strategic business asset, not an afterthought.
1. Policies Fail When They’re Static
Environments evolve. Policies must keep up.
- Have mobile access policies been updated for remote teams?
- Do vendor agreements reflect current security expectations?
- Are password rules aligned with identity management protocols?
2. Security Isn’t Just Tool-Based – It’s Procedural
Firewalls and monitoring aren’t enough if decision-makers don’t understand process gaps. Use this week to audit what’s documented versus what’s actually enforced.
3. Enforcement Is Often Inconsistent, Especially in Hybrid Environments
With split workforces, security posture depends on local behavior. Define clear standards across devices, work locations, and role levels.
4. Use National Internet Day to Reset Organizational Guardrails
Focus policy reviews on three dimensions: user behavior, third-party risk, and continuity planning.
| More articles you might like: |
The Myth of Connectivity: Why Uptime Without Oversight is a Liability
More access doesn’t mean better performance. National Internet Day often highlights speed, coverage, and convenience – yet none of these guarantee control. This section examines why growing connectivity requires proportional governance.
Too Much Access is Often Misread as Agility
Open systems make collaboration easier, but also make lateral movement faster for attackers.
- Audit integrations for scope creep
- Limit persistent access credentials
- Require internal sponsors for new connections
Idle Accounts Pose Active Threats
Unused accounts often go unnoticed during transitions. Review HR offboarding procedures, especially during seasonal turnover or post-M&A restructuring.
Connectivity Audits Should Be Built Into IT Roadmaps
- Document who has access to what, and why
- Require monthly reporting on account status changes
- Monitor for unapproved cloud service use
Without Oversight, Speed Becomes a Threat Multiplier
National Internet Day is a reminder that connection should be strategic, not assumed secure by default.
Connectivity Without Oversight vs. Strategic Connectivity: A Business-Level Comparison
| Dimension | Connectivity Without Oversight | Strategic Connectivity |
| Access Management | Shared credentials across platforms | Role-based access with periodic reviews |
| Cloud App Integration | Teams install tools without IT awareness | All integrations pass through a centralized approval |
| Offboarding Procedures | Inactive accounts linger for weeks or months | Accounts disabled within hours via automated triggers |
| Vendor Access Control | Long-term credentials remain active post-engagement | Temporary credentials with expiration and logging |
| Network Visibility | No clear audit of who connects where | Real-time monitoring and historical session tracking |
| Risk Ownership | Dispersed across teams, rarely documented | Clearly assigned to functional owners with review loops |
| Change Response Time | Delayed by unclear ownership and undefined protocols | Pre-scripted escalation paths with measured SLAs |
Making National Internet Day Count: 7 Executive Actions to Improve Resilience Today
Moments like National Internet Day provide a rare chance to slow down and reassess. This final section offers practical next steps for executive and IT leaders to turn reflection into action.
Start With a Focused Risk Snapshot
Review what changed in the last quarter.
- New systems
- New vendors
- Team or access changes
Evaluate Service Agreements for Clarity, Not Just Price
Contract language should define uptime, response time, and data ownership. Flag vague or outdated terms for legal review.
Run One Simulation – Then Document Everything
- Pick one critical failure scenario
- Test your response in real time
- Identify gaps, assign owners, update procedures
Improve IT Support Feedback Loops
82% of customers expect to get their IT issues solved within the first call. If you’re missing that mark, dig into ticket data – not just resolution time, but escalation trends and repeat issues.
Use This Week to Build a 90-Day Roadmap
Set three short-term actions tied to infrastructure, policy, and performance monitoring. Assign deadlines and revisit progress during the next board review.
Infrastructure Should Reflect the Way You Work – Not Slow It Down
Strategic security planning isn’t seasonal – it’s operational. Whether you’re managing routine support or mapping resilience, your systems should flex with your business, not fight against it.
| Explore our range of IT services in Calgary:
|
Contact us to reframe how your digital operations prepare for what’s next






