Network vulnerabilities are more than just technical oversights. They expose systems, data, and operations to deliberate attacks. Without strong oversight, these weak points allow bad actors to infiltrate, disrupt, and even hijack systems.
“A 2022 Sophos Report shows that 66% of organizations were hit by ransomware the previous year, despite having protection in place.”
Chad Cunningham, Owner and Partner of Ironclad TEK, emphasizes, “The reality is that attackers don’t need to break down the door, they just wait for someone to leave it open.”
In this blog, you’ll learn what makes network security vulnerabilities so dangerous, the most common network vulnerabilities to look for, and how cyber threats and vulnerabilities work together. You’ll also see how to prevent weak points before they lead to costly disruptions.
Close Up All the Blind Spots in Your Security
What Makes Network Security Vulnerabilities So Dangerous
A network vulnerability becomes dangerous when attackers can exploit it to gain unauthorized access, steal information, or disrupt services. These weak points, whether from misconfigurations or outdated systems, connect directly to many types of attacks in network security.
For example:
- Unpatched software leaves systems open to known exploits. If attackers know you haven’t updated your software, they can easily apply existing tools to break in.
- Unsecured endpoints like laptops and mobile devices often bypass strict internal controls. Without the right protection, they become the entry point that attackers use.
- Weak credentials, like reused or default passwords, make it easy for attackers to brute-force their way into systems.
Once attackers get in through these weaknesses, they can launch attacks like malware infections, data theft, or denial-of-service operations. One missed patch or misconfigured access rule can expose an entire network to serious risk.
Common Network Vulnerabilities That Attackers Exploit
In most business networks, common network vulnerabilities come from rushed deployments, inconsistent maintenance, or human oversight. These vulnerabilities open doors for attackers, whether they are criminals or nation-state actors.
Some of the most frequently exploited weak points include:
- Poor patch management: Delayed or missed updates keep known bugs alive in your system. Attackers scan for these bugs daily.
- Weak access controls: Too many users have unnecessary access, or there’s no multi-factor authentication. This increases the attack surface.
- Default system configurations: Leaving systems in their default state (including usernames and passwords) makes it easy for attackers to predict settings and break in.
Today’s hybrid work environments also introduce new threats:
- IoT devices: These often lack built-in security and are rarely updated. Attackers target them to gain a foothold inside the network.
- Remote work setups: Personal devices and unsecured Wi-Fi create weak spots attackers can use to enter business systems.
- Bring-your-own-device (BYOD) policies: Without strict controls, personal devices can become sources of information security vulnerabilities.
These aren’t theoretical risks. They are happening every day in organizations that don’t take consistent, preventive action.
Human-Centered Cybersecurity Vulnerabilities
65% of breaches are caused by external actors, while 35% stem from employee errors rather than malicious intent.
People make mistakes, and attackers know it. Cybersecurity vulnerabilities often originate with users, not systems. 75% of CISOs identify human error as the biggest cybersecurity risk.
Human-centred weaknesses include:
- Social engineering: This is when attackers manipulate people into giving up access. They might pretend to be IT staff or business partners.
- Phishing: Emails that look legitimate trick users into clicking malicious links or providing credentials. Some even mimic real invoices or HR notices.
- Poor user habits: Sharing passwords, using public Wi-Fi without VPNs, and failing to log out of accounts can open the door to serious threats.
These human behaviors contribute to information security vulnerabilities that technical controls alone cannot fix. Regular security training and policies are essential to reduce human-related risks.
Main Types of Network Security Threats You Should Know
There are many types of network security threats, each with different methods and impacts. Below are key threats you need to know about:
- Malware: This includes ransomware, spyware, Trojans, and keyloggers. Malware can lock systems, steal credentials, or spy on users without detection.
- Viruses and worms: These spread across systems, consuming resources and causing data loss. Unlike viruses, worms can self-replicate and move across networks without user interaction.
- Botnets and DDoS tools: Attackers infect devices to form a network (botnet) that can overwhelm services using distributed denial-of-service (DDoS) attacks.
- Man-in-the-middle attacks: These intercept communication between users and systems, allowing attackers to steal data or inject malicious content.
- SQL injections: Poorly secured web forms or applications allow attackers to run harmful database commands, exposing or deleting sensitive data.
Phishing methods: Beyond simple emails, phishing now includes voice calls (vishing), SMS (smishing), and fake websites.
| More articles you might like: |
How Cyber Threats and Vulnerabilities Work Together
No attack happens in isolation. Attackers combine different types of vulnerabilities in network security to break into systems and move laterally.
Consider this:
- A phishing email tricks a user into downloading a file.
- That file installs malware that scans the system for unpatched software.
- The malware spreads through unsecured endpoints and accesses databases using default credentials.
This is a blended attack, where one weak point opens up new opportunities for attackers. Failing to address even one vulnerability increases the chance of multiple threats succeeding.
How to Prevent and Monitor Network Vulnerabilities
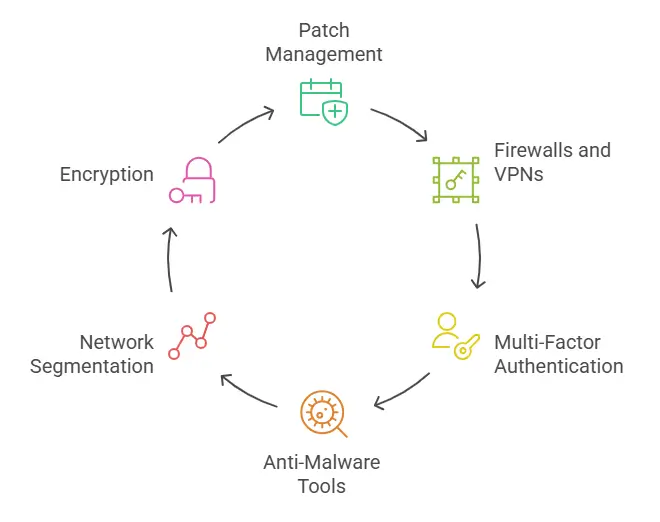
You don’t need to eliminate every vulnerability at once. You do need a layered strategy that prevents threats and gives you visibility into your network.
Some key steps include:
- Patch management: Maintain a schedule for updates. Apply patches as soon as they are released, especially for operating systems and core business apps.
- Firewalls and VPNs: Use firewalls to block unauthorized access and VPNs to encrypt data traffic across public networks.
- Multi-factor authentication (MFA): Require MFA for all accounts. This adds a layer of defense even if passwords are compromised.
- Anti-malware and endpoint tools: Use trusted software that actively scans and isolates threats before they spread.
- Network segmentation and encryption: Segment critical systems from general access networks. Encrypt all sensitive data in transit and at rest.
These practices reduce the surface area of attacks and help detect issues early before damage is done.
Why Physical Security Still Matters
Information security vulnerabilities aren’t always digital. Your physical environment can also be a weak point.
Examples include:
- Tailgating: Unauthorized persons enter secure areas by following employees.
- Unmonitored server rooms: Lack of surveillance or access control can result in tampering or theft.
- Stolen or misplaced devices: Laptops with sensitive information can be easily compromised if lost or stolen.
Secure doors, badge access systems, and device tracking policies are just as important as software controls.
Build a Culture of Cyber Vigilance Across the Organization
Technology alone can’t secure your network. Your people play a huge role. To stay ahead of cyber threats and vulnerabilities, you need a culture of constant awareness.
Start with these steps:
- Staff training: Teach employees to spot phishing and understand basic cyber hygiene. Run phishing simulations regularly.
- Clear security policies: Document rules around password use, remote work, and personal device access.
- Regular testing: Run vulnerability scans, penetration tests, and audits to catch issues before attackers do.
- Leadership support: Executives must back these efforts and model good security behavior.
Key Metrics to Track Vulnerability Exposure
To make sure you’re improving over time, monitor these key metrics. These indicators show how well you’re reducing your exposure to attacks.
| Metric | What It Measures | Why It Matters |
|---|---|---|
| Mean Time to Patch | Average days from patch release to install | Delays in project delivery, frustrated clients |
| Number of Critical Vulnerabilities | Total unresolved high-risk weaknesses | Lost contracts, reputational damage |
| Phishing Simulation Success Rate | % of users who fail the phishing email test | Indicates awareness levels and training effectiveness |
| Endpoint Coverage | Unused resources, higher bills | Low coverage exposes the network to malware and control loss |
Tracking these will help you make smarter, faster decisions about your security efforts.
Secure Your IT Infrastructure with Ironclad TEK Cybersecurity
Network vulnerabilities are fatal, and so should your defenses, when you stay proactive. In this blog, you’ve learned how various types of vulnerabilities in network security lead to real-world risks. You’ve also seen how poor practices, weak configurations, and human behavior contribute to cybersecurity vulnerabilities that attackers exploit.
Ironclad TEK helps organizations build secure and resilient systems. We currently support and protect over 1000 endpoints. With 20 years of IT and cybersecurity experience, our team identifies common network vulnerabilities, strengthens weak points, and supports your teams with the training and tools they need.
| Discover Reliable Cybersecurity Near You
|
Contact us today to schedule a consultation and see where your network stands.






